How to Secure Your Website with Web Application Firewalls
I. Introduction
A few years ago, I learned a lesson that changed my perception of website security entirely. My modest but growing website, a niche blog about vintage comic books, was hit by a sudden wave of bot traffic. Overnight, my site was sluggish, my genuine readers were frustrated, and my hosting service was threatening to suspend my account due to the sudden spike in traffic.
What was happening? As it turns out, my site was under a Distributed Denial of Service (DDoS) attack, a common form of cyber assault where multiple systems overwhelm the targeted system with traffic. It was my wake-up call to the importance of web security, and it led me to discover a powerful tool for protecting websites: the Web Application Firewall or WAF.
Now, you might be wondering, “What on earth is a WAF?” Let me put it simply. Imagine you’re throwing a house party. You’ve invited a bunch of friends, and you’re expecting them to show up at your door. But there’s a problem. Some uninvited guests are trying to crash your party. That’s where the bouncer comes in, someone who checks each person at the door, only letting in the people you’ve invited.
In this scenario, your website is the party, the visitors are your friends, and the bouncer is your WAF. Just like a bouncer, a WAF checks all incoming traffic, ensuring that only legitimate visitors get in while keeping out the undesirables like hackers and bots. It’s your website’s first line of defense, working tirelessly to keep your digital space safe and secure.
“But do I really need a bouncer for my website?” you might ask. Let’s consider the facts: In 2022 alone, approximately 64% of companies experienced at least one form of cyber attack. A successful attack can lead to data breaches, causing damage to your business reputation and potentially costing you a lot of money in reparations. By deploying a WAF, you’re significantly minimizing the risk of such incidents. So, the importance of a WAF for website security is akin to the importance of a helmet while riding a bike – it’s not just necessary, it’s essential.
In this blog post, we’re going to dive deeper into WAFs – why you need them, how to choose the right one for your website, and how to maintain them. Stick around, because we’re about to turn you into a website security aficionado!
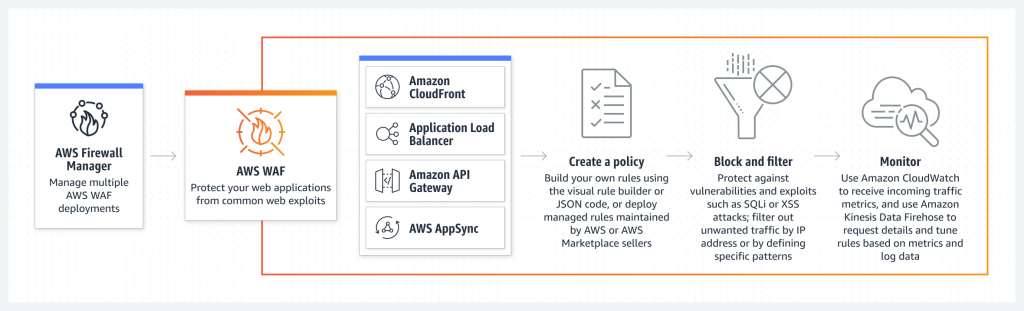
II. Understanding the Basics
(A) How Does a WAF Work?
Let’s simplify how a WAF works:
- Imagine a bodyguard at a party checking the guest list.
- The bodyguard only allows guests whose names are on the list.
- In the same way, a WAF checks every bit of traffic coming to your website.
- It lets in good traffic (like customers or search engines).
- It blocks bad traffic (like hackers or bots).
(B) What Threats Can a WAF Protect Against?
A WAF helps protect against several threats:
- SQL injections: Imagine a rigged letter that explodes in your mailbox when you open it. Similarly, hackers use SQL injections to mess with your website’s database, causing it to malfunction or reveal sensitive information.
- Cross-Site Scripting (XSS): Picture a flyer that makes you do things you didn’t want to do when you read it aloud. In a similar way, XSS tricks your website into running malicious scripts.
- Distributed Denial of Service (DDoS) attacks: Think of a crowd of pranksters blocking your door so you can’t get out of your house. DDoS attacks flood your website with so much traffic that it crashes.
(C) How is a WAF Different From Other Firewalls?
Here’s a comparison of a traditional firewall and a WAF:
- A traditional firewall is like a fence around your property. It stops trespassers but can’t do much about threats that come through the gate, like rigged letters.
- A WAF is more specialized. It guards against common threats and specifically protects against application-level threats. So it keeps the pranksters away and also checks every letter coming through the mail.
(D) What are the Main Types of WAFs?
There are different types of WAFs to consider:
- Network-Based WAFs: These are robust and fast, like fortress walls around a medieval city. However, they can be expensive and challenging to set up.
- Host-Based WAFs: These are integrated within your web server, offering great customization, like installing security cameras inside your house. But they can use a lot of your system’s resources and require a lot of upkeep.
- Cloud-Based WAFs: These are like hiring a security service. They’re easy to set up and affordable. They provide round-the-clock protection but require trust in your provider.
| Network-Based WAFs | Host-Based WAFs | Cloud-Based WAFs | |
|---|---|---|---|
| Ease of Setup | Difficult | Moderate | Easy |
| Cost | High | Varies (usually moderate) | Low to Moderate |
| Resource Usage | Low (offloads processing to network hardware) | High (runs on the same server as the web application) | Low (processed in the cloud) |
| Protection Level | High | High | High |
| Maintenance | Requires professional IT staff | Requires moderate IT knowledge | Low (handled by provider) |
| Scalability | Limited by hardware capabilities | Limited by server resources | Highly Scalable (handled by provider) |
| Latency | Low (processed locally) | Low (processed locally) | Varies (can be low with regional data centers) |
| Customizability | Moderate | High | Moderate |
The type of WAF you choose will depend on your specific needs and resources.
III. Why You Need a Web Application Firewall
(A) Real-World Cases of Security Breaches
Let me tell you a story that happened with a friend of mine. She ran a small online store for handmade crafts. One day, her website was attacked with what’s known as a DDoS attack – an overwhelming wave of traffic that crashed her site. It took several days to get the website back up, and during that time, she lost sales, frustrated her customers, and took a serious hit to her brand’s reputation.
But it’s not just small businesses at risk. You’ve probably heard of big companies like Yahoo, eBay, or Equifax being hit by cyberattacks. These breaches can lead to the theft of sensitive data, like user passwords or credit card numbers. Even giants aren’t immune to this.
Let’s look at some cases that hit the headlines. In 2013, Target, a major US retailer, suffered a security breach that compromised the data of 41 million customers. The breach was traced back to a single point of failure in their security. As a result, Target’s reputation took a hit, and they had to pay a $18.5 million settlement.
Similarly, Equifax, one of the largest credit bureaus in the U.S., experienced a breach in 2017. It exposed the personal data of 147 million people and cost the company over $4 billion in total.
In both cases, a well-configured Web Application Firewall could have made it significantly more difficult for the attackers to gain access.
(B) The Potential Cost of Ignoring Website Security
The cost of a security breach isn’t just about immediate losses or repairing the damage. There’s also the ripple effect. Picture this – you’re hosting a party, but the gate crashes open, and a herd of goats storms in, causing chaos. Even once the goats are gone, you still have to deal with the mess left behind. That’s what a cyberattack is like.
On a financial level, these are some costs you might face:
- Loss of sales: When your site is down, you can’t sell. Simple as that.
- Cost of recovery: Fixing the breach and restoring your site isn’t free.
- Fines or lawsuits: If customer data was leaked, you could face legal penalties.
Non-financial costs are also significant:
- Damage to reputation: Customers lose trust in a business after a security breach.
- Loss of customer data: If customer data is stolen, it can lead to a loss of customers.
- Lower SEO rankings: Google may lower the rankings of sites that have been hacked.
(C) How a WAF Can Save You Money
Imagine a strong gate that keeps the goats out but lets your party guests in freely. That’s what a WAF does for your website. It can save you money by preventing security breaches that could lead to the costs we just discussed. The investment in a WAF is much less than the potential costs of a major security incident.
More than just preventing loss, a WAF also adds value:
- Improved website performance: Some WAFs can optimize content delivery, making your site load faster for visitors.
- Boost SEO: A secure and optimized website can improve your SEO rankings.
- Customer trust: Users are more likely to trust and do business with a site they know is secure.
In the long run, a WAF isn’t just a cost – it’s an investment in your website’s success.
| Case Study | Incident Date | Breach Description | Vulnerabilities Exploited | How a WAF Could Have Helped |
|---|---|---|---|---|
| Target | December 2013 | Attackers stole credit/debit card details and customer contact information. | Network intrusion through a third-party HVAC vendor’s access. Malware was placed on the POS system. | A WAF could have identified and blocked suspicious network traffic and helped prevent the spread of malware. |
| Equifax | July 2017 | Personal data of 143 million consumers was exposed, including names, Social Security numbers, birth dates, addresses, and driver’s license numbers. | Exploited a vulnerability in a web application framework Apache Struts. The vulnerability was known and a patch was available but not implemented. | A WAF could have detected the exploitation attempt on the known vulnerability and blocked it, preventing the data leak. |
IV. Choosing the Right Web Application Firewall
So, we’ve established that you need a Web Application Firewall, but which one? Let’s break down the decision-making process and turn it into something more digestible. Remember, choosing a WAF isn’t about finding the “best” one, but finding the right one for you.
A. What to Look for in a WAF
When shopping for a WAF, here are some key features to keep an eye out for:
- Ease of Deployment: Whether you’re a tech whizz or not, a WAF that’s easy to set up and configure can save you a lot of headaches.
- Threat Coverage: Look for a WAF that protects against a wide range of threats, including SQL injection, XSS, and CSRF attacks, just to name a few.
- Customizability: A good WAF allows you to set custom rules for your website’s specific needs.
- Regular Updates: The world of cyber threats is constantly evolving, and so should your WAF.
- Reporting and Analytics: A user-friendly dashboard that provides detailed insights about traffic and threats can be a valuable tool.
- Customer Support: If things do go wrong, it’s essential to have a support team you can rely on.
B. Comparing Popular WAF Providers
Choosing a WAF can feel like a game of “spot the difference”. Let’s make it easier with this handy comparison table:
| WAF Solution | Deployment Type | Protocol Support | DDoS Protection | AI/ML Capabilities | Integration | Pricing |
|---|---|---|---|---|---|---|
| Imperva WAF | Both on-premises and cloud | Supports HTTP, HTTPS, APIs, and more | Included | Yes | Integrates with various tools | Starts at $59/site/month |
| Cloudflare | Cloud-based | Supports HTTP, HTTPS, and others | Included | Yes | Works well with DevOps tools | Pro plan at $20/month |
| Microsoft Azure App Gateway | Cloud-based | Supports HTTP, HTTPS, and more | Included | Yes | Ideal for Azure services | Pay-as-you-go |
| AWS WAF | Cloud-based | Supports HTTP, HTTPS, and more | Included | Yes | Good fit for AWS services | Starts from $5/month |
| Barracuda WAF | Both on-premises and cloud | Supports HTTP, HTTPS, and more | Included | Yes | Compatible with various tools | Begins at $1.02 per unit |
(Remember, prices and features may vary and it’s always good to check with the provider directly)
C. Checklist for Choosing the Right WAF
Lastly, here are some questions to ask yourself when deciding on a WAF:
- What threats do I most need to protect against?
- What’s my budget?
- Do I need a solution that’s easy to deploy and manage?
- Are regular updates and customer support important to me?
- What kind of traffic volume am I dealing with?
- Do I have any specific integration needs?
Remember, the goal isn’t to answer all these questions perfectly. Instead, it’s about finding a balance that works best for you and your website.
Phew! It’s quite a lot to digest, isn’t it? But don’t worry, by considering these factors and examining your specific needs, you’re well on your way to making an informed decision. Happy hunting for the right WAF!
V. How to Install and Configure a WAF
Congratulations on choosing a Web Application Firewall (WAF) to protect your website! Now, let’s dive into the installation and configuration process so you can get your WAF up and running smoothly.
A. Setting Up Your WAF: Step-by-Step Guide
- Choose Your WAF Provider: Select a reputable WAF provider that aligns with your needs and budget.
- Create an Account: Sign up for an account on the provider’s website. Provide the necessary details and complete the registration process.
- Add Your Website: Within your account dashboard, locate the option to add your website. Follow the instructions to link your domain to the WAF.
- Configure DNS: Update your domain’s DNS settings to point to the WAF provider’s servers. This step ensures that all traffic passes through the WAF for inspection and filtering.
- Adjust WAF Settings: Access the WAF settings page and customize the security rules according to your website’s requirements. Consider enabling features like SQL injection protection, cross-site scripting prevention, and rate limiting to enhance your defenses.
- Activate the WAF: Once you’ve adjusted the settings, activate the WAF for your website. This step marks the beginning of your website’s protected journey.
Pro tip: Many WAF providers offer detailed installation guides, tutorials, and even video walkthroughs to assist you throughout the setup process. Take advantage of these resources for a smoother experience.
Step-by-step guide on how to install and configure a Web Application Firewall (WAF) for some popular WAF providers.
AWS WAF –https://docs.aws.amazon.com/waf/latest/developerguide/getting-started.html
Barracuda WAF – https://campus.barracuda.com/product/webapplicationfirewall/doc/4259915/step-1-installing-the-barracuda-web-application-firewall/
B. Maximizing Security with Configuration Settings
Configuring your WAF involves more than just turning it on. Let’s explore some important settings to maximize your website’s security:
- Threat Detection Sensitivity: Adjust the sensitivity level of the WAF to strike the right balance between identifying genuine threats and avoiding false positives.
- Whitelisting and Blacklisting: Create whitelists and blacklists to explicitly allow or block certain IP addresses or specific types of traffic.
- HTTP Headers: Review and modify the HTTP headers sent by your website to enhance security and protect against common vulnerabilities.
- File Upload Policies: Define strict policies for file uploads, including file size limits and allowed file types, to prevent malicious uploads.
- Bot Protection: Enable bot protection features to detect and block automated malicious activities, such as content scraping or brute-force attacks.
Remember, the specific configuration options may vary depending on the WAF provider. Consult the provider’s documentation or support resources for detailed instructions on adjusting these settings.
C. Testing Your WAF: Ensuring Effectiveness
Once your WAF is configured, it’s crucial to verify its effectiveness. Here are some tips for testing:
- Simulate Attacks: Attempt various attack techniques, such as SQL injection or cross-site scripting, to see if your WAF correctly detects and blocks them.
- Monitor Logs and Alerts: Keep an eye on the WAF logs and alert notifications to ensure that any suspicious activity triggers the appropriate responses.
- Regularly Review Reports: Analyze reports generated by the WAF to identify patterns, potential vulnerabilities, and areas that require further fine-tuning.
- Stay Updated: Regularly check for WAF updates and apply them promptly to benefit from the latest security enhancements.
| Configuration Setting | Practical Implications |
|---|---|
| Threat Detection Sensitivity | Adjusting sensitivity levels helps fine-tune the WAF’s ability to detect and block threats. A higher sensitivity may catch more threats, but it can also lead to more false positives. Finding the right balance ensures accurate threat detection while minimizing disruptions to legitimate traffic. |
| Whitelisting and Blacklisting | Implementing whitelists and blacklists allows you to control access to your website. Whitelisting trusted IP addresses ensures only authorized entities can access your site, while blacklisting suspicious IP addresses blocks potential threats. This helps prevent unauthorized access and mitigates risks associated with malicious actors. |
| HTTP Headers | Modifying HTTP headers provides an extra layer of protection. For example, implementing Content Security Policy (CSP) headers helps prevent cross-site scripting (XSS) attacks by defining allowed sources for scripts, stylesheets, and other resources. By configuring strict HTTP headers, you enhance your website’s resilience against common vulnerabilities and protect user data. |
| File Upload Policies | Setting strict file upload policies helps prevent malicious files from being uploaded to your server. By limiting file size, restricting allowed file types, and scanning uploads for malware, you reduce the risk of hosting and distributing malicious content. This protects your website and its visitors from potential harm. |
| Bot Protection | Enabling bot protection features helps detect and block automated malicious activities, such as content scraping or brute-force attacks. By distinguishing between legitimate users and malicious bots, you can prevent abusive behavior, maintain the integrity of your website, and safeguard sensitive data. |
By testing your WAF and staying proactive, you can be confident in your website’s security defenses and respond swiftly to emerging threats.
Setting up and configuring a WAF may seem daunting, but with the right guidance, it becomes a manageable task. Remember, your efforts to secure your website are worth it, and a WAF provides an added layer of protection against potential attacks. Stay vigilant and keep your online presence safe.
VI. Best Practices for Maintaining Your WAF
Now that your Web Application Firewall (WAF) is up and running, it’s important to maintain its effectiveness and keep your website secure. Here are some practical best practices for maintaining your WAF:
A. Keeping Your WAF Updated
Regular updates are crucial for maintaining the security of your WAF. But how often should you update it? Here’s a simple guideline:
- Stay Informed: Keep an eye on your WAF provider’s website, blog, or newsletters for announcements about updates, new features, or security patches. They often release updates in response to emerging threats.
- Follow Recommended Guidelines: Most WAF providers recommend updating your WAF at least once a month or whenever critical security vulnerabilities are identified. This ensures you have the latest protections against known threats.
- Balance Timeliness and Impact: While it’s important to update promptly, ensure you have enough time to test the updates in a non-production environment. This minimizes any potential disruption to your live website.
Remember, updates are not just about new features but also about addressing vulnerabilities. By keeping your WAF updated, you ensure it remains robust and effective against evolving threats.
B. Monitoring Your WAF
To maximize the benefits of your WAF, it’s essential to monitor its performance and understand the data it provides. Here’s a simple guide to monitoring your WAF effectively:
- Review Traffic Patterns: Regularly analyze your WAF’s traffic logs and reports. Look for any unusual spikes or patterns that could indicate an ongoing attack or suspicious activity.
- Identify Threats: Pay attention to the WAF’s alerts and notifications. These warnings signal potential threats or malicious attempts to breach your website’s security.
- Understand False Positives: False positives occur when legitimate traffic is flagged as a threat. Learn to distinguish between false positives and real threats to prevent blocking legitimate users.
- Fine-Tune Rules: Periodically review and adjust your WAF’s rules based on the observed patterns and feedback from your website’s users. This ensures a balance between security and seamless user experience.
By monitoring your WAF diligently, you can proactively identify and address potential security issues, keeping your website protected.
C. Staying Informed about New Threats and WAF Updates
Cyber threats are constantly evolving, and staying informed is crucial to maintaining your website’s security. Here are some strategies for staying up-to-date:
- Follow Security Blogs and News: Subscribe to reputable security blogs, forums, or newsletters to receive the latest information about emerging threats, vulnerabilities, and WAF best practices.
- Engage in Online Communities: Join online communities or forums where security professionals and website owners share insights and discuss the latest trends. Collaborating with peers can help you stay informed and learn from others’ experiences.
- Utilize Threat Intelligence Feeds: Consider integrating threat intelligence feeds into your WAF. These feeds provide real-time information about known threats and help enhance your WAF’s effectiveness.
- Regularly Check for WAF Updates: Visit your WAF provider’s website or support resources to stay informed about the latest updates, new features, and security enhancements. Keeping your WAF up to date ensures you have the most effective protection against evolving threats.
By leveraging these strategies, you can proactively protect your website and respond effectively to emerging threats.
Remember, maintaining your WAF is an ongoing process. By following these best practices, you ensure that your WAF remains effective, adaptive, and resilient in the face of ever-evolving cybersecurity challenges. Stay informed, stay vigilant, and keep your website secure.
VII. Advanced Tips
As you become more familiar with Web Application Firewalls (WAFs), you can explore advanced features and strategies to enhance your website’s security. Let’s dive into some practical advanced tips:
A. Exploring Advanced WAF Features
WAFs offer advanced features that can provide extra layers of protection for your website. Here are a few key features explained in simple terms:
- Bot Management: Advanced WAFs incorporate bot management capabilities to differentiate between legitimate users and malicious bots. These features use machine learning algorithms to identify and block suspicious bot activity, ensuring your website remains accessible to genuine users.
- API Protection: As web applications increasingly rely on APIs, WAFs with API protection capabilities can safeguard your API endpoints from unauthorized access, data leaks, and attacks. This feature prevents security vulnerabilities in your API layer, ensuring the integrity of your data and interactions.
- Behavioral Analysis: Advanced WAFs employ behavioral analysis techniques to identify anomalous user behavior and detect sophisticated attacks. By monitoring patterns, such as unusual request rates or suspicious session activity, the WAF can proactively block potential threats.
- Virtual Patching: WAFs can apply virtual patches to known vulnerabilities in web applications. This allows you to protect against exploits even before the underlying application is updated, reducing the window of vulnerability.
B. Troubleshooting Common WAF Issues
While WAFs are designed to enhance security, occasional issues may arise. Here are some common WAF issues and troubleshooting tips:
- False Positives: False positives occur when legitimate traffic is mistakenly identified as malicious and blocked. To address this, review your WAF’s logs and fine-tune rules to minimize false positives without compromising security.
- Performance Impact: In some cases, WAFs can impact website performance. If you experience performance issues, consider optimizing your web application or adjusting your WAF’s configuration to strike the right balance between security and performance.
- Compatibility Challenges: Certain web applications or frameworks may require special configurations or exemptions in your WAF rules. If you encounter compatibility challenges, consult your WAF provider’s documentation or support resources for guidance.
C. Scaling Your WAF as Your Website Grows
As your website expands, it’s essential to scale your WAF to accommodate increased traffic and evolving threats. Here are some strategies for scaling your WAF effectively:
- Monitor Traffic Patterns: Keep a close eye on traffic trends and patterns. Spikes in traffic or changes in user behavior may indicate the need to adjust your WAF’s capacity or configurations.
- Regularly Assess Security Posture: Conduct periodic security assessments to identify any gaps or vulnerabilities. This allows you to make informed decisions about upgrading or adjusting your WAF settings to align with your website’s evolving needs.
- Consider Load Balancing: Distributing traffic across multiple servers using load balancing techniques can help scale your WAF’s capacity and handle increased user demand. Explore load balancing options compatible with your WAF provider.
By leveraging advanced features, troubleshooting effectively, and scaling your WAF as needed, you can stay one step ahead of potential threats and ensure your website’s ongoing security as it grows.
Remember, advanced tips require a solid understanding of your WAF’s capabilities and your website’s unique requirements. Implement these tips gradually, keeping a balance between security, performance, and user experience.
VIII. Conclusion
In conclusion, securing your website with a Web Application Firewall (WAF) is a critical step in safeguarding your online presence. By implementing a WAF, you protect your website from various threats, ensure continuous monitoring, and have the ability to customize security measures according to your specific needs.
Remember to regularly update and maintain your WAF, staying informed about emerging threats and implementing best practices. Monitor your website’s traffic and analyze logs to identify potential issues or attacks. And most importantly, take action and secure your website today.
With a WAF in place, you can have peace of mind knowing that your website is fortified against malicious activities, providing a safe and secure experience for your users. Stay proactive, stay vigilant, and keep your website protected.

