What to Know About Email Security and Encryption
1. Introduction
Welcome to our digital world, where communication is a click away, and so are potential threats. Consider this – a report from Cybint suggests that a whopping 156 million phishing emails are sent worldwide every single day. Yes, you read it right, every single day! This glaring statistic underscores the urgent need for stronger email security and encryption in our interconnected environment.
So, what’s at stake here? Why should you even bother about email security? Well, let’s get real. Our emails are a treasure trove of valuable data, from personal to professional information, which makes them a hot target for cybercriminals. The lack of robust security measures is akin to leaving your house’s doors unlocked and inviting thieves over for dinner. Not quite the scenario you’d fancy, right?
Pro Tip: Did you know that email security breaches have been on the rise? According to recent statistics, over 90% of cyberattacks start with an email. By highlighting this impactful statistic, you can grab your readers’ attention and emphasize the importance of email security from the get-go.
But worry not! Email encryption comes to our rescue. It’s like your personal security guard, ensuring your confidential emails are read only by the intended recipients, keeping all eavesdroppers at bay.
In this blog post, we’re going to demystify:
- The concept and importance of email security.
- The common threats looming over your emails.
- How email encryption plays a key role in safeguarding your data.
- The steps you can take to enhance your email security.
By the end of this guide, you’ll have a practical understanding of email security and encryption, and be equipped with actionable steps to protect your data. So, let’s dive in, and together, make our digital communication a safer space!
II. Deciphering Email Security
With a world increasingly connected online, understanding the concept of email security has become as essential as knowing how to send an email itself. So, let’s jump right into it.
Email security is the set of procedures and techniques used to safeguard your email accounts and content from unauthorized access, loss, or compromise. Simply put, it’s about ensuring that the emails you send and receive reach their intended destination without being intercepted, altered, or misused.
Think of email security as the bouncer of your digital communication world. It verifies the identity of everyone who tries to gain access, decides who gets in, and importantly, who doesn’t.
But why is all of this necessary? Here’s why:
- Confidentiality: Your emails may contain sensitive information – from business strategies to personal data. Without proper email security, you risk exposing this information to cybercriminals.
- Trust: When your email is secure, it builds trust with your contacts, knowing that their information is safe with you.
- Regulation Compliance: If you handle customer data, you need to comply with privacy laws. A solid email security system can help meet these requirements.
Despite these reasons, people often overlook the need for robust email security, which can lead to some substantial risks, including:
- Data Breach: Unsecured emails can lead to the exposure of sensitive information.
- Phishing Attacks: Without proper security measures, you’re more susceptible to phishing scams that could lead to financial loss or identity theft.
- Loss of Reputation: A security breach can significantly harm your personal or corporate reputation.
Pro Tip: According to research, inadequate email security measures can result in an average data breach cost of $3.86 million. It’s crucial to prioritize email security to avoid these costly consequences and protect your sensitive information.
Understanding the above, you probably have a few questions buzzing in your head. Let’s answer some frequently asked ones.
Your Email Security FAQs
- Q: Is a strong password enough for email security? A: While a robust and unique password is a good start, it’s not sufficient on its own. Incorporating other security measures, like two-factor authentication and email encryption, can provide comprehensive protection.
- Q: If I use a popular email service provider, are my emails automatically secure? A: Not necessarily. While renowned email service providers do offer various security features, it’s up to you to ensure they’re activated and used correctly.
- Q: Can’t my antivirus software take care of email security? A: Antivirus software can protect against threats like malware, but it doesn’t typically encrypt your emails or protect against all types of phishing attempts.
In essence, email security isn’t a luxury – it’s a necessity in our digitized world. By understanding its importance and the potential risks of negligence, you’re one step closer to making your digital communication safer and more secure. Let’s keep the momentum going!
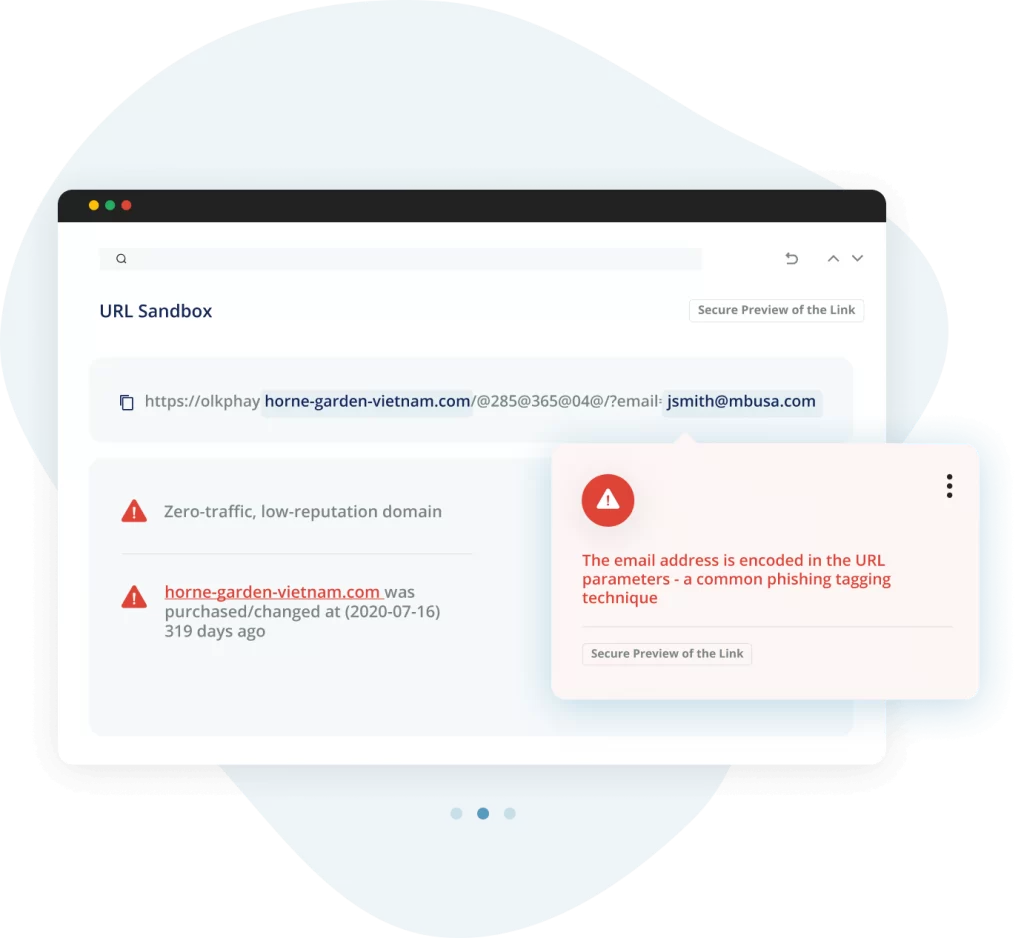
III. Threats in the Email Landscape
In the vast expanse of digital communication, emails have become fertile ground for cyber threats. To navigate this landscape effectively, it’s essential to recognize the most common types of threats and their potential impacts. Here’s your guide through the terrain.
The Most Common Email Threats
There are several types of email threats that you may encounter. Let’s break them down in an easily digestible format:
- Phishing: These are deceitful emails designed to trick you into revealing sensitive information, such as your password or credit card number. They often appear to come from a trustworthy source, but don’t be fooled!
- Spam: We’ve all been there – an inbox flooded with unsolicited emails, often promotional. Although seemingly harmless, some spam emails may contain malicious links or attachments, serving as a vehicle for more severe threats.
- Malware: Short for malicious software, malware includes harmful entities like viruses, ransomware, and spyware. They usually hitch a ride with seemingly innocent email attachments or links.
- Spoofing: Spoofing attacks occur when a cybercriminal impersonates another person or organization, usually to trick the recipient into performing a specific action.
- Man-in-the-Middle Attack (MitM): In a MitM attack, the attacker secretly intercepts and possibly alters the communication between two parties.
Pro Tip: Over 90% of successful cyberattacks start with a phishing email. Understanding the types and impacts of common email threats is essential to avoid falling victim to these malicious attempts.
To give you a clearer picture, imagine these threats as different species in the jungle of email security. You can visualize them in a table or chart form:
| Email Threat Type | Description | Potential Risks |
|---|---|---|
| Phishing | Fraudulent emails from seemingly reputable sources | Identity theft, financial loss |
| Spam | Unsolicited messages sent in bulk | Wasted time, a gateway for other threats |
| Malware | Malicious software like viruses, ransomware, spyware | Data loss, system damage |
| Spoofing | Impersonation of another individual or organization | Loss of sensitive data, financial loss |
| Man-in-the-Middle Attack (MitM) | Secret interception and possible alteration of communication | Exposure of sensitive information, altered communication |
Real-world Consequences of Poor Email Security
Cyber threats are not abstract concepts – they have tangible, often disastrous, impacts. To illustrate, let’s look at some real-world examples:
- Yahoo Data Breach (2013-2014): One of the largest data breaches in history occurred when Yahoo’s network was compromised, affecting nearly 3 billion users. Personal data was stolen, and Yahoo’s reputation suffered immensely.
- WannaCry Ransomware Attack (2017): An email-based malware attack affected hundreds of thousands of computers across 150 countries. The financial impact was in the billions, proving that no one is safe from the threat of cybercrime.
These incidents underline the dire need for robust email security. As we venture further into this topic, keep in mind the various threats that lurk in the shadows of your inbox and the potential consequences of ignoring them. Stay safe, and let’s continue the journey!
IV. An In-depth Look at Email Encryption
As we delve deeper into the world of email security, it’s time to shine a light on one of its most crucial cornerstones: email encryption. Like a secret code used between two friends, encryption ensures that only the intended recipients can decode and understand the content of an email. Let’s crack this code together.
Understanding Encryption: The Language of Locks and Keys
Imagine you’ve written a secret note that you only want your best friend to read. To prevent anyone else from reading it, you come up with a special code that only you and your friend understand. Now, even if someone else gets their hands on the note, they won’t understand it unless they know the code. This is the essence of encryption.
In the world of email security, encryption transforms the content of an email into a ‘coded language’, unreadable to anyone without the right ‘key’ to decode it. This process ensures that only the intended recipient, who has the correct ‘key’, can read the email’s content.
The Role of Encryption in Email Security
By translating your email content into this secure code, encryption plays a vital role in maintaining the confidentiality and integrity of your information. Here’s how:
- Confidentiality: Your email’s content remains private and is only accessible to the intended recipient, preventing unauthorized individuals from understanding the message even if they intercept it.
- Integrity: Encryption also ensures the content of the email remains unchanged during transmission. It verifies that the message received by the recipient is exactly the one you sent, with no alterations.
Pro Tip: Studies show that implementing email encryption can reduce the risk of data breaches by up to 80%. By leveraging encryption, you can significantly enhance the confidentiality and integrity of your email content.
Email Encryption: A Mini Glossary
To make our journey easier, let’s arm ourselves with some key encryption-related terms:
- Cipher: The ‘coded language’ used in encryption.
- Key: A string of characters used for encryption and decryption.
- Public Key: A key that is available to everyone and is used to encode messages.
- Private Key: A key that only the recipient has access to, and is used to decode messages.
- End-to-End Encryption (E2EE): A system of communication where only the communicating users can read the messages.
| Email Encryption Tool/Service | Features | Compatibility |
|---|---|---|
| PGP (Pretty Good Privacy) | End-to-end encryption, digital signatures | Windows, Mac, Linux, iOS, Android |
| S/MIME (Secure/Multipurpose Internet Mail Extensions) | Message encryption, certificate-based authentication | Windows, Mac, iOS, Android |
| ProtonMail | End-to-end encryption, zero-access encryption | Web-based, iOS, Android |
| Virtru | Client-side encryption, access controls | Windows, Mac, iOS, Android |
| Tutanota | End-to-end encryption, secure password recovery | Web-based, iOS, Android |
By understanding the language of email encryption, we strengthen our defenses and enhance our skills in navigating the email security landscape. Remember, encryption isn’t an abstract tech jargon—it’s our secret code, our lock, and key in the vast world of digital communication. Ready to take the next step? Let’s march on!
V. Implementing Email Encryption
Now that you understand the significance of email encryption, it’s time to put that knowledge into action. In this chapter, we’ll walk you through a comprehensive guide on implementing encryption, empowering you to secure your emails like a pro.
1. Understanding the Basics of Email Encryption
Before diving into the implementation process, it’s crucial to grasp the fundamentals. Encryption can be implemented in different ways, so let’s explore two common options:
- Inbuilt Encryption Features: Many popular email services, such as Gmail and Outlook, offer built-in encryption features. These features typically include options like TLS (Transport Layer Security) for encrypting email transmission and S/MIME (Secure/Multipurpose Internet Mail Extensions) for end-to-end email encryption.
- Standalone Encryption Software: If your email service doesn’t provide built-in encryption or you prefer more advanced encryption options, standalone encryption software is an excellent alternative. Popular standalone encryption software includes PGP (Pretty Good Privacy) and GPG (GNU Privacy Guard).
2. Step-by-Step Implementation Guide
Now, let’s get practical. Follow this step-by-step guide to implementing email encryption:
Task 1: Enable Inbuilt Encryption Features (Gmail)
- Step 1: Sign in to your Gmail account.
- Step 2: Go to “Settings” by clicking on the gear icon in the top right corner.
- Step 3: Navigate to the “See all settings” option.
- Step 4: In the “General” tab, scroll down to the “Confidential mode” section.
- Step 5: Enable “Confidential mode” to send emails with additional security options like expiration dates and requiring passcodes for access.
Task 2: Set Up S/MIME Encryption (Outlook)
- Step 1: Open Outlook and go to “File” in the top left corner.
- Step 2: Select “Options” and then choose “Trust Center” from the left sidebar.
- Step 3: Click on the “Trust Center Settings” button.
- Step 4: In the Trust Center dialog box, select “Email Security” from the left sidebar.
- Step 5: Click on “Settings” in the “Encrypted email” section.
- Step 6: Follow the prompts to configure your S/MIME certificate, including importing or generating a certificate.
Task 3: Using PGP Encryption (Standalone Encryption Software)
- Step 1: Install PGP software such as Gpg4win (for Windows) or GPG Suite (for Mac).
- Step 2: Generate your PGP key pair, consisting of a public key for encryption and a private key for decryption.
- Step 3: Share your public key with trusted contacts and import their public keys as well.
- Step 4: Use the PGP software to encrypt your outgoing emails and decrypt incoming encrypted emails.
VI. Proactive Measures for Enhanced Email Security
Securing your emails is an ongoing process that requires proactive measures to stay ahead of potential threats. In this chapter, we’ll equip you with practical tips to fortify your email security defenses and ensure a safer digital communication experience.
1. Strengthening Email Security: Practical Tips
Here are some actionable steps you can take to enhance your email security:
- Use Strong and Unique Passwords: Create strong passwords that include a combination of upper and lowercase letters, numbers, and symbols. Avoid using common passwords or reusing them across multiple accounts.
- Enable Two-Factor Authentication (2FA): Activate 2FA for your email accounts to add an extra layer of protection. This requires a second verification step, such as a unique code sent to your phone, in addition to your password.
- Beware of Phishing Attempts: Be cautious of suspicious emails requesting personal information or containing unexpected attachments or links. Double-check the sender’s email address and be wary of urgency or threats in the message content.
- Regularly Update Software and Devices: Keep your email client, operating system, and antivirus software up to date to ensure you have the latest security patches and protections against known vulnerabilities.
- Be Mindful of Public Wi-Fi: Avoid accessing sensitive emails or entering login credentials when connected to unsecured public Wi-Fi networks. Use a virtual private network (VPN) for a secure connection when necessary.
2. Email Security Checklist
To assist you in implementing these security measures effectively, we’ve prepared a downloadable email security checklist. This comprehensive checklist serves as a handy reference to ensure you’ve covered all the essential bases. It includes:
- Password best practices
- Two-Factor Authentication setup instructions
- Tips for identifying phishing attempts
- Software and device update reminders
- Guidance on secure Wi-Fi usage
By following this checklist, you can systematically enhance your email security and reduce the risks associated with cyber threats.
VII. Glimpse into the Future of Email Security
As technology continues to advance, the realm of email security is constantly evolving. In this chapter, we’ll explore the upcoming trends and advancements that shape the future of email security.
1. AI and Machine Learning: Transforming Email Security
AI and Machine Learning (ML) are set to revolutionize the way we approach email security. Here’s what you need to know:
- Advanced Threat Detection: AI-powered systems can analyze vast amounts of data to detect patterns and anomalies, enabling more accurate identification of sophisticated threats like phishing attacks and malware.
- Behavioral Analysis: ML algorithms can learn from user behavior, helping systems identify abnormal activities and potential security breaches more effectively.
- Automated Incident Response: AI can streamline incident response by automating processes, enabling quicker identification and mitigation of security incidents.
2. The Role of Technology in Email Security
As technology continues to evolve, so do the tools and techniques used to safeguard email communications. Keep an eye on these emerging trends:
- End-to-End Encryption: The demand for end-to-end encryption, which ensures that only the sender and recipient can access the email content, is on the rise. This added layer of security will become increasingly prevalent.
- Enhanced Authentication Methods: Traditional username and password authentication are being supplemented with more secure methods like biometrics, hardware keys, and multi-factor authentication to strengthen email security.
- Cloud-Based Security Solutions: Cloud-based email security services offer centralized protection, advanced threat intelligence, and scalability, making them an attractive option for organizations seeking comprehensive email security solutions.
Pro Tip: Share an intriguing insight supported by data, such as “Experts predict that by 2025, AI-driven email security solutions will prevent 99% of advanced email threats. Keeping abreast of these upcoming trends can help you stay ahead of cyber threats and protect your email communications.
3. Embracing a Secure Future
To stay ahead in the ever-changing landscape of email security, it’s important to embrace a proactive and adaptive mindset. Here are a few steps you can take:
- Continuous Education: Stay informed about the latest email security threats, best practices, and technological advancements through reputable sources, blogs, and industry publications.
- Regular Security Assessments: Conduct periodic security assessments to identify vulnerabilities in your email infrastructure and implement necessary measures to mitigate risks.
- Collaboration and Information Sharing: Foster a culture of collaboration and information sharing within your organization and with industry peers to stay updated on emerging threats and effective countermeasures.
By embracing these future-oriented trends and adopting proactive measures, you can navigate the ever-evolving email security landscape with confidence.
VIII. Conclusion
In conclusion, remember that email security is an ongoing process that requires proactive measures and continuous vigilance. By implementing the practical tips and strategies outlined in this blog post, you can bolster your email security defenses and protect your sensitive information.
Secure email communications are not just a necessity; they are a fundamental right. As you navigate the digital landscape, prioritize the adoption of encryption, the implementation of strong security practices, and the commitment to ongoing education.
Together, let’s foster a secure email environment where trust and confidentiality thrive. Take charge of your email security today, and enjoy the peace of mind that comes with safeguarding your digital communications.


